[Google Notification]
What’s happening?
Starting January 16th, 2018, Google Play will block publishing of any new apps or updates that contain this path traversal vulnerability. Your published APK version will remain unaffected, but any updates to the app will be blocked if the vulnerability is present.
Action required.
There are two recommended strategies for eliminating a path traversal vulnerability in a ContentProvider.
If your ContentProvider does not need to be exposed to other apps:
You can modify the tag of the affected ContentProvider in your Manifest to set android:exported="false". This will prevent other apps from sending Intents to the affected ContentProvider.
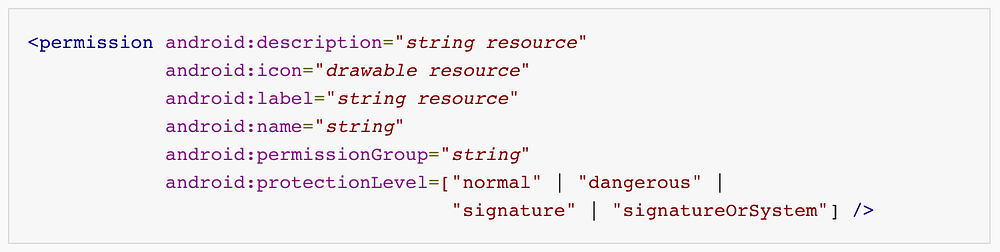
You can also set the android:permission attribute to be a permission with android:protectionLevel="signature" to prevent apps written by other developers from sending Intents to the affected ContentProvider.
If your ContentProvider needs to be exposed to other apps:
Confirm that inputs to openFile which contain path traversal characters cannot cause your app to return unexpected files. You can do this by checking the file's canonical path.
Implementations of openFile in exported ContentProviders can be vulnerable if they don't properly validate incoming Uri parameters. A malicious app can supply a crafted Uri (for example, one that contains “/../”) to trick your app into returning a ParcelFileDescriptor for a file outside of the intended directory, which allows the malicious app to access any file accessible to your app.
Next steps
Update your app using the steps highlighted above.
Sign in to your Play Console and submit the updated version of your app.
Check back after five hours. We'll show a warning message if the app hasn't been updated correctly.
[Solution]
- Remove possibility of other apps accessing your app's files (setting exported="false")
- Allow access only to apps with your signature (basically only to your other apps) - protectionLevel="signature"

I'll post the real case as step by step.
Android Developer Link :
https://developer.android.com/guide/topics/manifest/provider-element.html?hl=ko#exported
'Programing > Debugging' 카테고리의 다른 글
| [Android] INSTALL_PARSE_FAILED_NO_CERTIFICATES (0) | 2017.10.23 |
|---|---|
| [Error] Corona SDK - Google traversal vulnerability in a ContentProvider [Real Case] (0) | 2017.10.13 |
| Could not create the java virtual machine (0) | 2017.04.10 |
| Permissions on /var/www/html for uploading web site files via SFTP (0) | 2016.11.25 |
| [Android Gradle] How to check Gradle Distributions (0) | 2016.09.15 |



